Think of Enlightn as your performance and security consultant. Enlightn will "review" your code and server configurations, and give you actionable recommendations on improving performance, security and reliability!
The Enlightn OSS (open source software) version has 64 automated checks that scan your application code, web server configurations and routes to identify performance bottlenecks, possible security vulnerabilities and code reliability issues.
Enlightn Pro (commercial) is available for purchase on the Enlightn website and has an additional 64 automated checks (total of 128 checks).
- 🚀 Performance Quick Wins (In-Built In Laravel): Route caching, config caching, etc.
- ⏳ Performance Bottleneck Identification: Middleware bloat, identification of slow, duplicate and N+1 queries, etc.
- 🍽️ Serving Assets: Minification, cache headers, CDN and compression headers.
- 🎛️ Infrastructure Tuning: Opcache, cache hit ratio, unix sockets for single server setups, etc.
- 🛸 Choosing The Right Driver: Choosing the right session, queue and cache drivers for your app.
- 🏆 Good Practices: Separate Redis databases for locks, dont install dev dependencies in production, etc.
- 🔒 Basic Security: Turn off app debug in production, app key, CSRF protection, login throttling, etc.
- 🍪 Cookie Security and Session Management: Cookie encryption, secure cookie attributes, session timeouts, etc.
- 🃏 Mass Assignment: Detection of mass assignment vulnerabilities, unguarded models, etc.
- ☢️ SQL Injection Attacks: Detection of raw SQL injection, column name SQL injection, validation rule injection, etc.
- 📜 Security Headers: XSS, HSTS, clickjacking and MIME protection headers.
- 📁 Unrestricted File Uploads and DOS Attacks: Detection of directory traversal, storage DOS, unrestricted file uploads, etc.
- 💉 Injection and Phishing Attacks: Detection of command injection, host injection, object injection, open redirection, etc.
- 📦 Dependency Management: Backend and frontend vulnerability scanning, stable and up-to-date dependency checks, licensing, etc.
- 🧐 Code Reliability and Bug Detection: Invalid function calls, method calls, offsets, imports, return statements, syntax errors, etc.
- 💪 Health Checks: Health checks for cache, DB, directory permissions, migrations, disk space, symlinks, Redis, etc.
- ⚙️ Detecting Misconfigurations: Cache prefix, queue timeouts, failed job timeouts, Horizon provisioning plans, eviction policy, etc.
- 👻 Dead Routes and Dead Code: Detection of dead routes and dead/unreachable code.
- 🏅 Good Practices: Cache busting, Composer scripts, env variables, avoiding globals and superglobals, etc.
Each of the 128 checks available are well documented. You can find the complete 137 page documentation here.
You may install Enlightn into your project using the Composer package manager:
composer require enlightn/enlightnAfter installing Enlightn, you may publish its assets using the vendor:publish Artisan command:
php artisan vendor:publish --tag=enlightnNote: If you need to install Enlightn Pro, visit the documentation on the Enlightn website here.
After installing Enlightn, simply run the enlightn Artisan command to run Enlightn:
php artisan enlightnYou may add the --report flag, if you wish to view your reports in the Enlightn Web UI besides the terminal:
php artisan enlightn --reportIf you wish to run specific analyzer classes, you may specify them as optional arguments:
php artisan enlightn Enlightn\\Enlightn\\Analyzers\\Security\\CSRFAnalyzer Enlightn\\EnlightnPro\\Analyzers\\Security\\DirectoryTraversalAnalyzerNote that the class names should be fully qualified and escaped with double slashes as above.
If you want to get the full Enlightn experience, it is recommended that you at least run Enlightn once in production. This is because several of Enlightn's checks are environment specific. So they may only be triggered when your app environment is production.
In case you don't want to run on production, you can simulate a production environment by setting your APP_ENV to production, setting up services and config as close to production as possible and running your production deployment script locally. Then run the Enlightn Artisan command.
By default, the enlightn Artisan command highlights the file paths, associated line numbers and a message for each failed check. If you wish to display detailed error messages for each line, you may use the --details option:
php artisan enlightn --detailsIf you wish to integrate Enlightn with your CI, you can simply trigger the --ci option when running Enlightn in your CI/CD tool:
php artisan enlightn --ciYou may add the --report flag if you wish to view your CI reports in the Enlightn Web UI. Remember to add your project credentials to your config/enlightn.php file as explained here.
php artisan enlightn --ci --reportEnlightn pre-configures which analyzers can be run in CI mode for you. So, the above command excludes analyzers that need a full setup to run (e.g. analyzers using dynamic analysis).
For more information on CI integration, refer the Enlightn documentation.
Sometimes, especially in CI environments, you may want to declare the currently reported list of errors as the "baseline". This means that the current errors will not be reported in subsequent runs and only new errors will be flagged.
To generate the baseline automatically, you may run the enlightn:baseline Artisan command:
php artisan enlightn:baselineIf you wish to run this command in CI mode, you can use the --ci option:
php artisan enlightn:baseline --ciFor more information on establishing a baseline, refer the docs.
Enlightn offers a beautiful Web UI dashboard where you can view your Enlightn reports triggered from your CI or scheduled command runs.
The web UI is free for all users and includes the following:
- Statistics on pass percentages (overall and by category).
- All failed checks along with code snippets related to the checks (if any).
- Metrics on number of new and resolved issues (compared with the most recent report running on the same app URL, environment and project).
To get access to the Web UI, all you need to do is signup for free on the Enlightn website and follow the instructions mentioned here.
Besides integrating Enlightn with your CI/CD tool, it's a good practice to schedule an Enlightn run on a regular frequency (such as daily or weekly) like so:
// In your app/Console/Kernel.php file:
/**
* Define the application's command schedule.
*
* @param \Illuminate\Console\Scheduling\Schedule $schedule
* @return void
*/
protected function schedule(Schedule $schedule)
{
$schedule->command('enlightn --report')->runInBackground()->daily()->at('01:00');
}This will allow you to monitor Enlightn's dynamic analysis checks, which are typically excluded from CI. The reports can be viewed on the Enlightn Web UI.
Enlightn offers a GitHub bot that can prepare a report highlighting failed checks and also add review comments for pull requests on the lines of code that introduce new issues.
To integrate with the Enlightn GitHub bot, refer the docs.
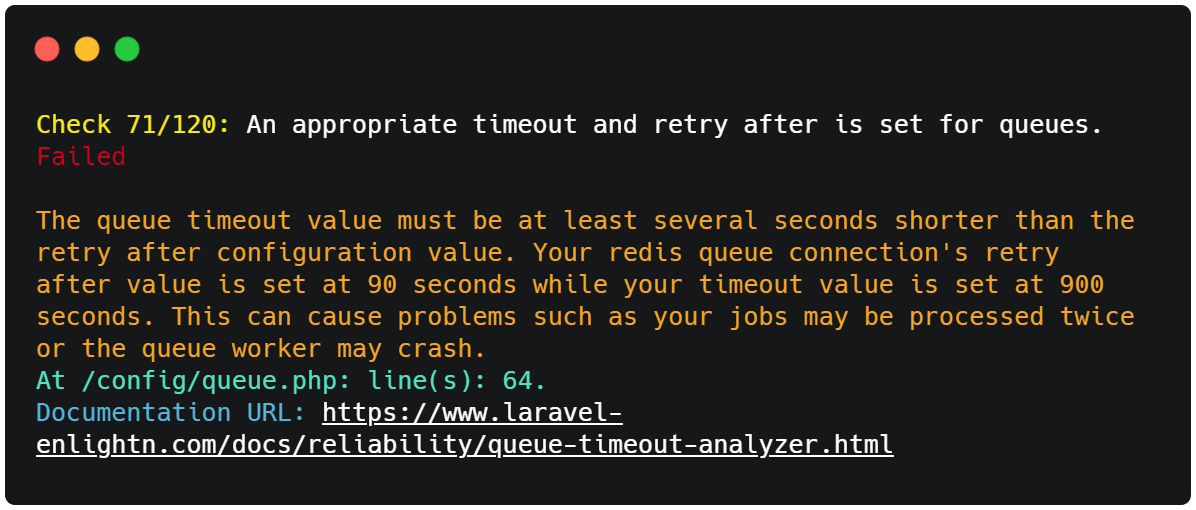
All checks that fail will include a description of why they failed along with the associated lines of code (if applicable) and a link to the documentation for the specific check.
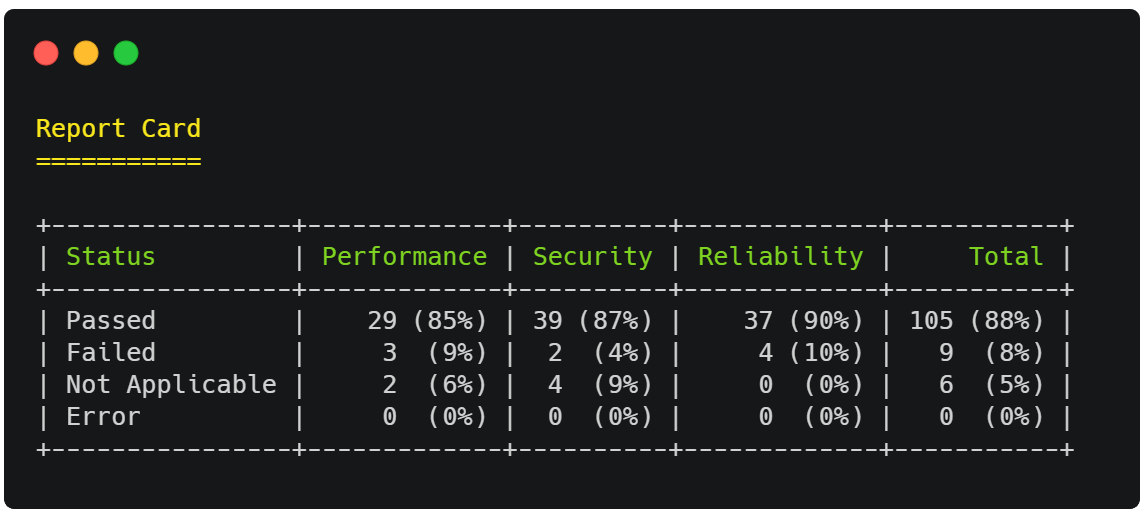
Finally, after all the checks have run, the enlightn Artisan command will output a report card, which contains information on how many and what percentage of checks passed, failed or were skipped.
The checks indicated as "Not Applicable" were not applicable to your specific application and were skipped. For instance, the CSRF analyzer is not applicable for stateless applications.
The checks reported under the "Error" row indicate the analyzers that failed with exceptions during the analysis. Normally, this should not happen but if it does, the associated error message will be displayed and may have something to do with your application.
A good practice would be to run Enlightn every time you are deploying code or pushing a new release. It is recommended to integrate Enlightn with your CI/CD tool so that it is triggered for every push or new release.
Besides the automated CI checks, you should also run Enlightn on a regular frequency using a scheduled console command as described above. This will allow you to monitor the dynamic analysis checks, which are typically excluded from CI.
Only MacOS and Linux systems are supported for Enlightn. Windows is currently not supported.
Thank you for considering contributing to Enlightn! The contribution guide can be found here.
Our support policy can be found in the Enlightn documentation.
The Enlightn OSS (on this GitHub repo) is licensed under the LGPL v3 (or later) license.
Enlightn Pro is licensed under a commercial license.